UK Government to fine for inadequate cyber security
The Guardian reported yesterday on a new legal threat for firms in the United Kingdom: huge fines for cyber security failures. Why would the government decide to add insult to injury? The goal is to force companies to get their act together.
Increasing pressure
We reported earlier on the rise of ransomware and noted just yesterday in our announcement of a ransomware protection app the massive costs to business these attacks can have. These attacks have also hit the National Health Service, causing significant disruption to public services. The UK government is now looking for ways to increase pressure on companies to implement preventive measures and improve processes of dealing with cyber attacks.
While bugs in code and their consequences are to some degree inevitable, there is a lot organizations can do to prevent their infrastructure from attacks and to react adequately once a breach has taken place. The goal of the new penalties is thus not to punish those who, despite all effort, get hacked. Rather, it is to increase the cost for those who decided not to invest in prevention and protection.
If, thus, a major cyber attack results in disruption to services such as transport, health or electricity, an investigation is started. If it is concluded that the victim of the cyber attack had failed to take measures to prevent or deal with security failures, a fine of up to 4% of yearly turnover can be given.
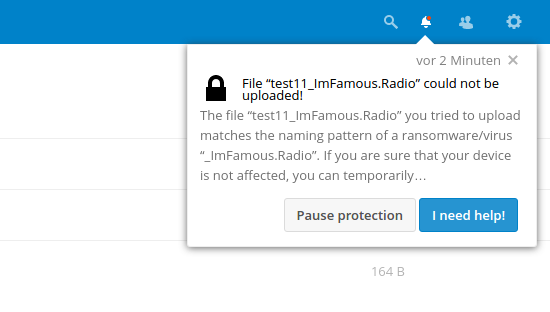
Notification of potential ransomware in Nextcloud
How to protect your business
This is merely another reminder of the growing threats businesses face. Picking the right technologies to depend on is the first and perhaps most important step in protecting your infrastructure.
Sadly, vendors are often hostile to security researchers reporting vulnerabilities. Many invest little beyond what gets them marketing attention.
Here are a few factors to consider to avoid such vendors:
- Does the vendor develop its software in a secure way? A transparent process with security reviews of new designs, code reviews and use of pentesting tools all help avoid bugs in the process of writing code.
- Have these processes been verified by an independent third party? It is worth downloading a report and flipping through it and checking what the conclusions were.
- Is there a public Security Bug Bounty program with relevant payouts? On security platforms like HackerOne you can easily check statistics of responsivity and payments, giving you an idea of how serious a vendor takes security.
- How is their security track record? Security mistakes are rarely heavily advertised but you can often find reports by independent researchers complaining their findings were not taken seriously. Or you find issues mentioned and discussed on prominent security lists like the famous Full Disclosure list. A search in the archives can be enlightening!
And a last point: encryption is great. Modern encryption cyphers are rarely broken. Instead, crypto is bypassed! Amazon’s Kindle and Samsung Galaxy protections were bypassed by replacing the key or remove the signature checking code. Bad development practices and a lack of security reviews isn’t fixed with encryption!
I love crypto, it tells me what part of the system not to bother attacking
— Drew Gross, forensic scientist