User management
Easy account management, from 5 to 50 million users
Integrated account management
Nextcloud features integration with external user directories like LDAP, Active Directory or others as well as built-in account management, two-factor authentication and Single-sign-on support.
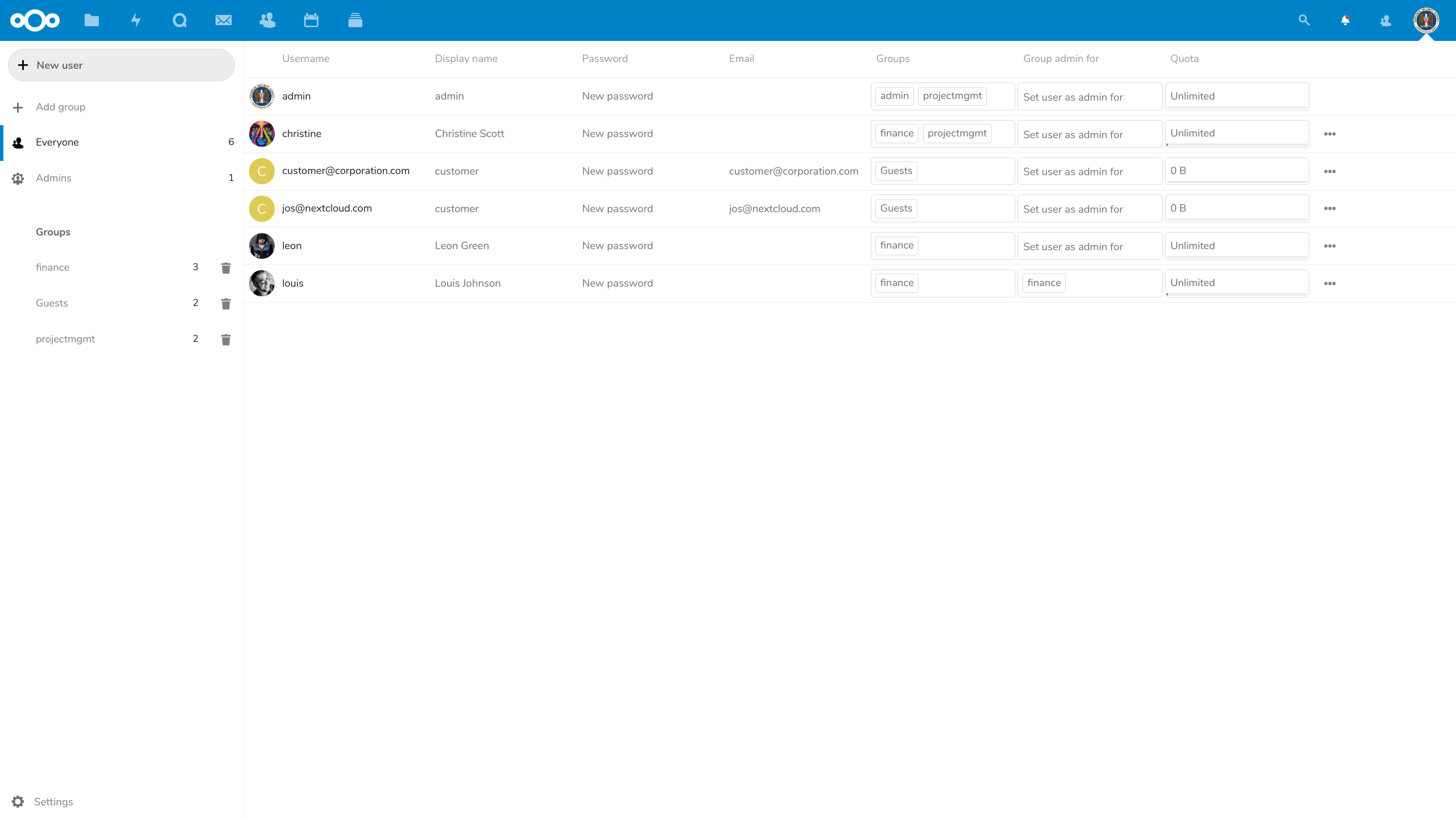
Easy user management
Admins can create, modify, search and view user accounts using Nextcloud built-in user management. Name, disk quota, mail addresses and group membership can be handled and users can be given administrator privileges if needed.
If you need to integrate Nextcloud with an existing system, take advantage of support for one or more LDAP directories instead of or in addition to local users. Nextcloud can secure logins with two-factor authentication and supports single sign-on through SAML, OAuth2, Kerberos and others.
For large-scale solutions, performance optimization, additional tools and advice, see the Nextcloud customer portal.
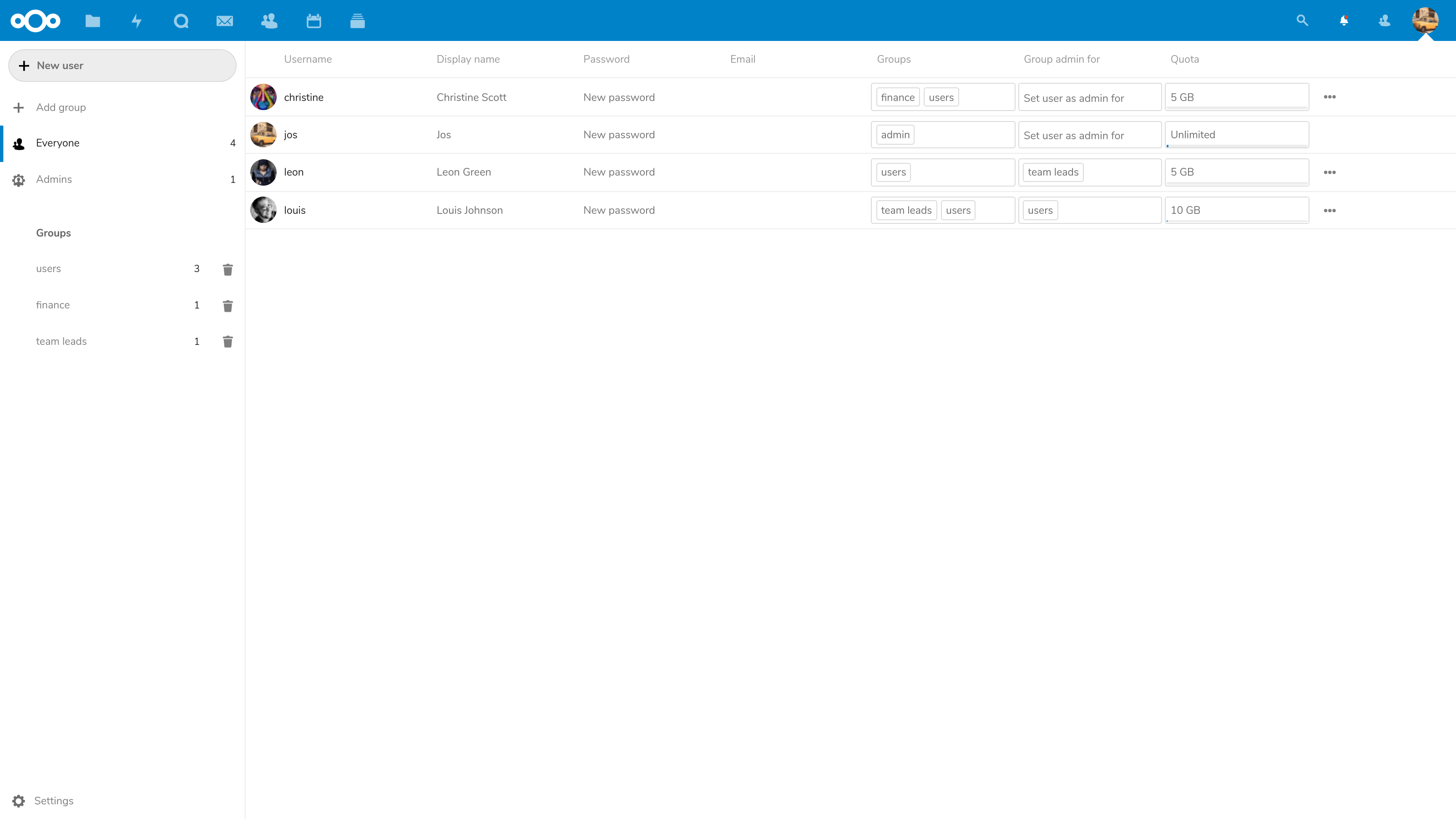
Group admins
The administrator can delegate some work by elevating some accounts to group administrator over specified groups. This allows them to create new users as members of these groups as well as delete and modify them.
When enabled, group admins can also create 2-factor one-time login codes and do other administrative tasks like manage ACLs on Groupfolders.
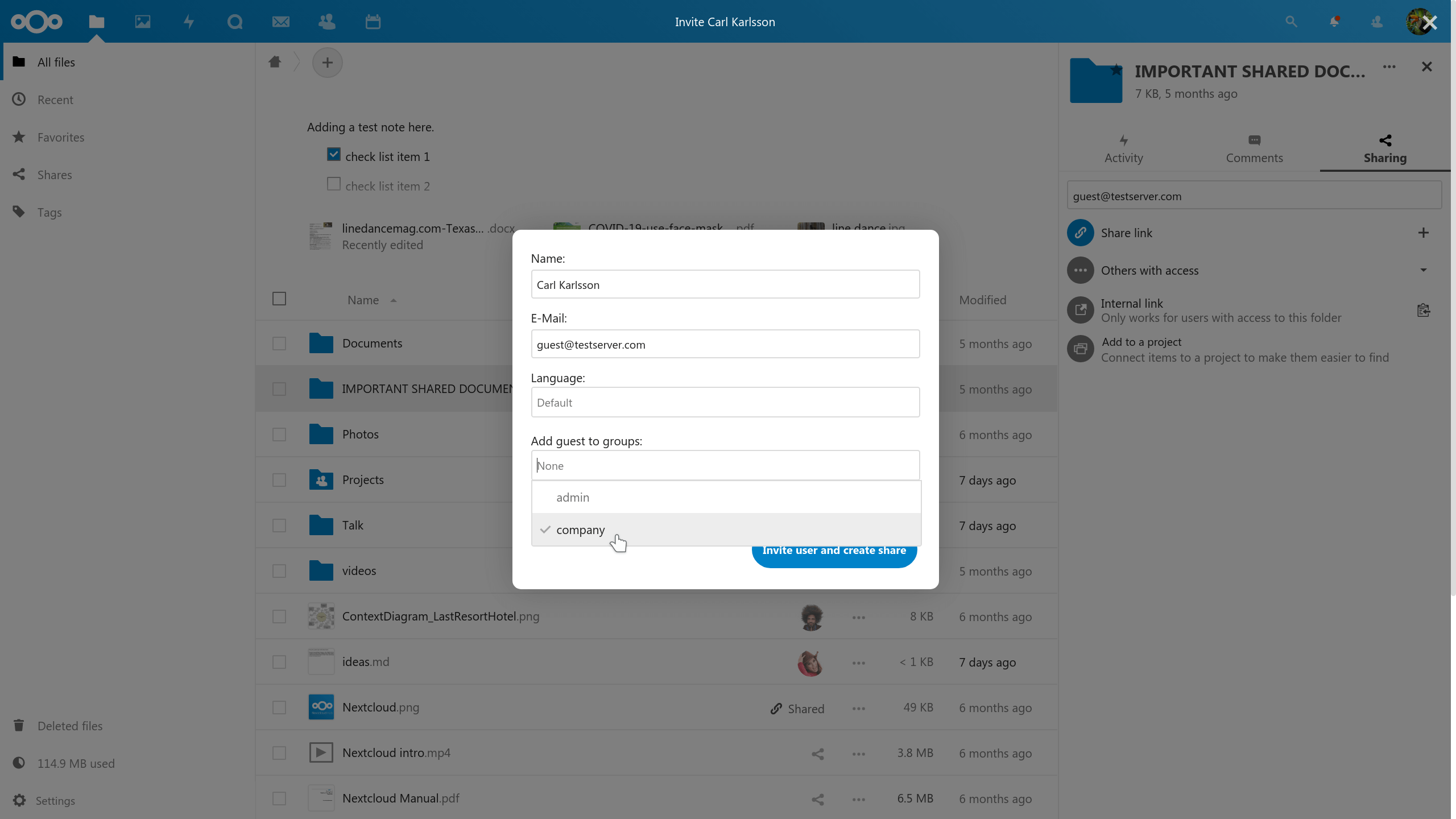
Guest accounts
The guest accounts app enables users to create guest accounts for recipients. The administrator can determine what access rights these users need to have to external storage and apps.
As guests have a special (hidden) group, administrators can use the Workflow and File Access Control capabilities to restrict, for example, users from downloading or sharing data. In Virtual Dataroom scenarios guest accounts can be given access to data read-only or with editing rights while blocking downloads and watermarking all files. Documents can shared with them through the Secure Mailbox feature from the Nextcloud Outlook Add-in which prevents the mail body and attachments from leaking.
Upon creation, users can designate a group to a guest account.
Workflow and file access controlPassword security enforcement
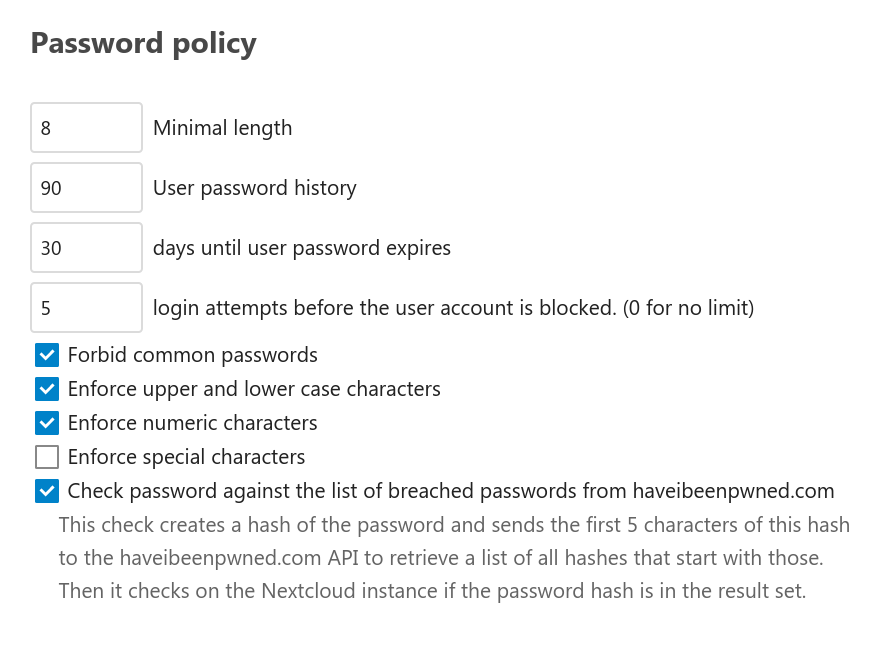
Password security is extremely important and Nextcloud follows the latest and most strict standards.
We go beyond these standards, checking passwords against the database of compromised accounts and passwords from well known security researcher Troy Hunt. This optional but highly recommended feature ensures users can not reuse a password which has been compromised on another website already. Read our blog to learn how this feature protects your users.
Blog on HaveIBeenPwnedAdd accounts easily with a QR code
See how easy it is for a Nextcloud user to add new accounts on their mobile devices.
Our powerful clients are among the best rated file sync and share clients in the industry and easy to use!
Learn about our clientsUser-defined group management
Users can define their own, custom groups, named Circles. These can be managed in various ways, including with invitations, through an open listing where users can join with or without an approval step, with designated sub-managers and so on.
Users can share with these groups the same way as administrator-defined Nextcloud groups. Users can add members of a circle to a conversation, share a folder to a circle, assign a task to a circle and so on.
Remote Wipe
While Nextcloud supports Mobile Device Management solutions, thanks to built-in support, remote wipe will work on systems not under management of the company. This is useful for home users but also large universities and of course in a scenario where guest accounts were handed to a third party. If you permit downloading of documents by the third party, you can wipe the documents from their devices when the the collaboration has ended.
Remote wipe can be used on a per-device basis by users and on a per-user base by the administrator.
Learn more about how Nextcloud helps you keep your data secure.
Security in NextcloudLDAP/Active Directory user management
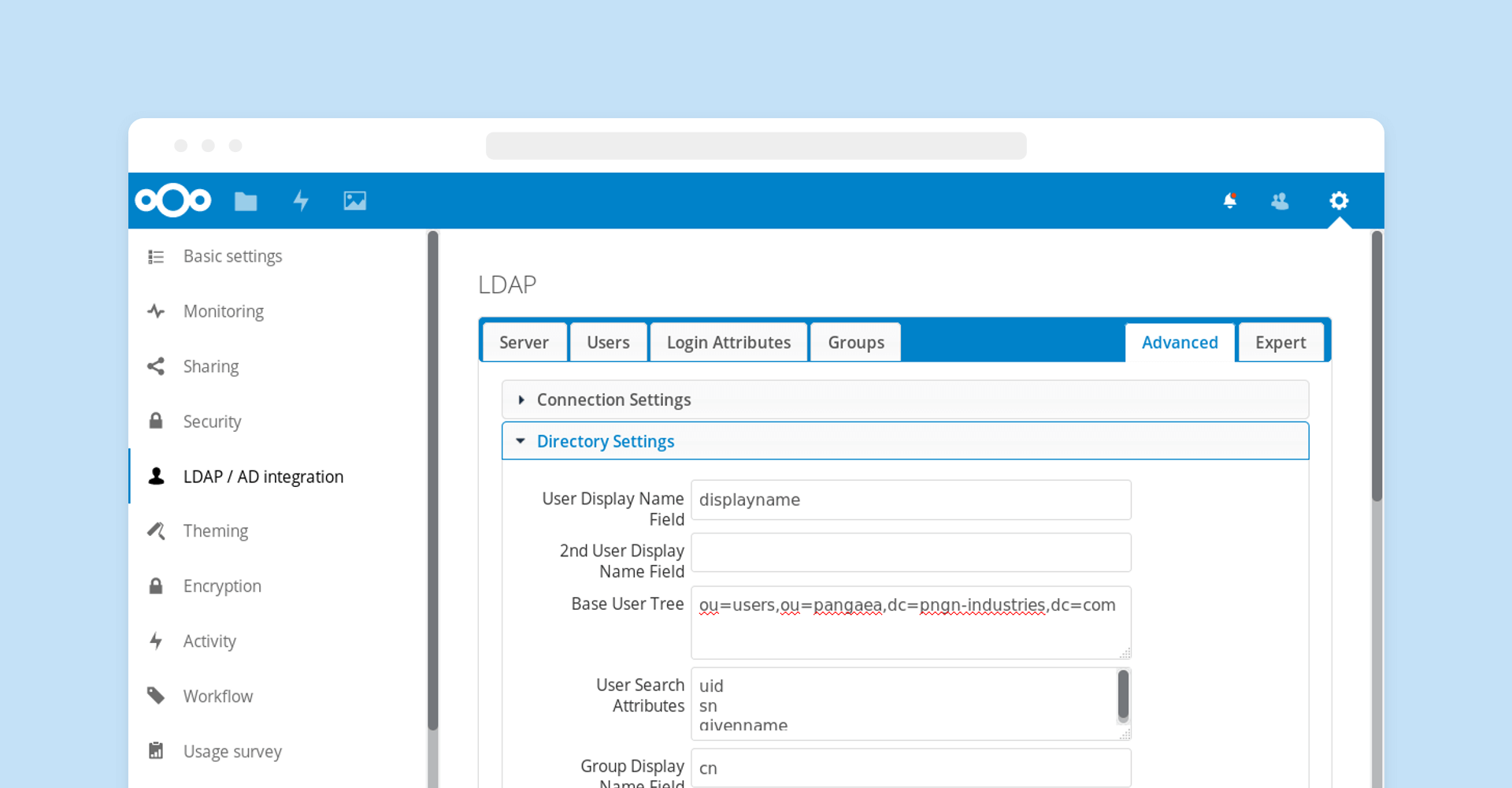
Nextcloud features a high performance, full-featured LDAP application which lets users authenticate through their LDAP credentials. Group management, quotas and sharing permissions can be managed as usual. Nextcloud features LDAP group support, sharing, primary groups and easy configuration with auto-detection of LDAP attributes.
For security reasons, the default LDAP configuration is fully read-only. Creating, updating and removing LDAP configurations can optionally be done through an external, REST-based API.
Nextcloud also supports limited LDAP/AD account management, enabling admins to create, modify or delete users in the connected user directory. Through a plugin-infrastructure, more capabilities can be added.
Download our LDAP whitepaperAutomated or manual provisioning
Nextcloud offers an easy-to-use, REST-based provisioning API to create and configure user accounts. It is possible to create, edit, delete and query user attributes, query, set and remove groups, set quota and query total storage used in Nextcloud.
The API enables an admin to query for active Nextcloud applications, application info, and to enable or disable an app remotely. HTTP requests can be used via a Basic Auth header to easily integrate workflows with existing tools and infrastructure.
API documentationMulti-factor authentication
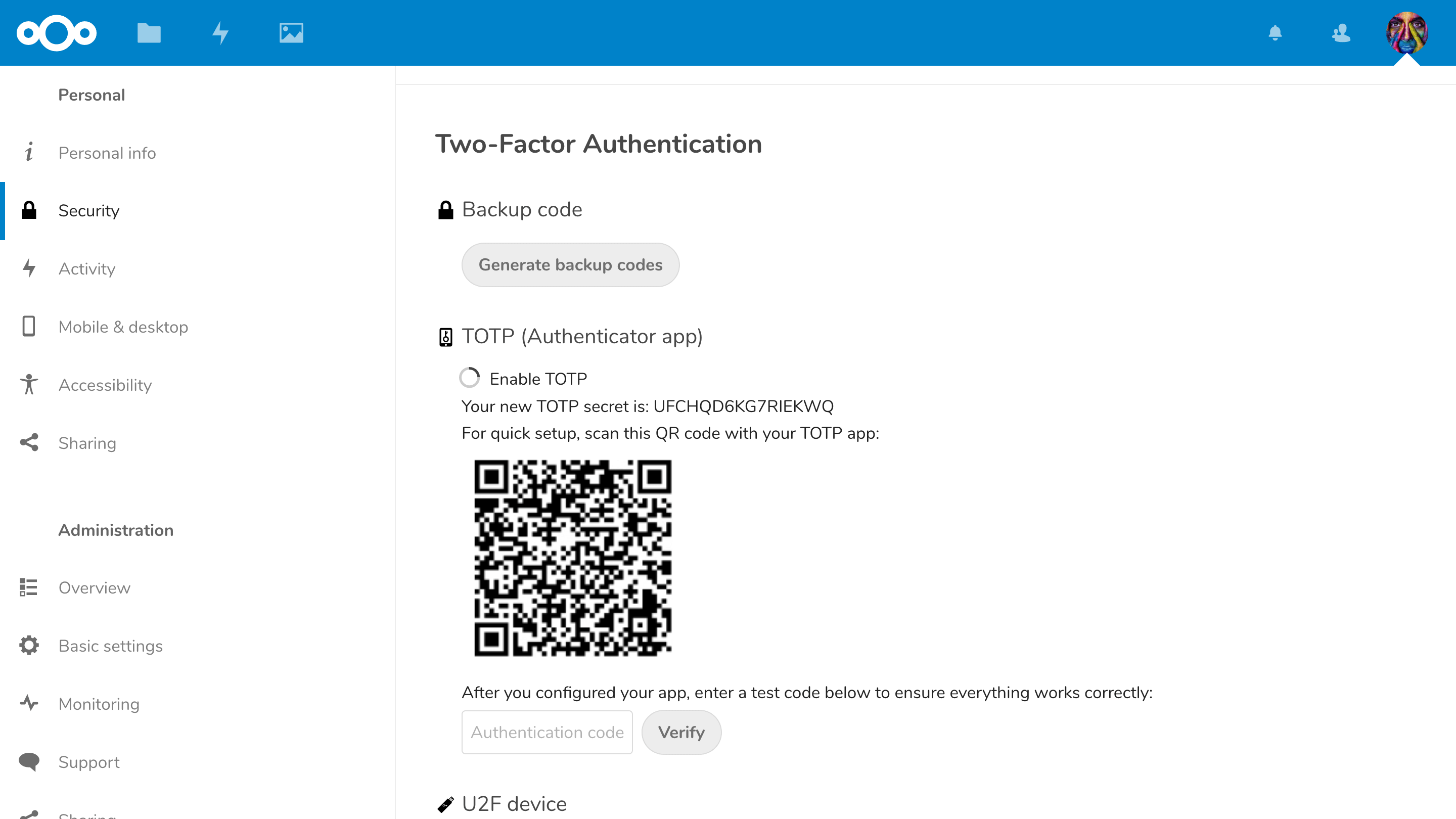
Nextcloud supports a wide variety of second factors and allows admins to enforce use of 2-factor authentication.
Second factors:
- Time-based One-Time Password (TOTP, including Google Authenticator or similar apps
- Universal 2nd Factor hardware tokens (U2F, like Yubikeys or Nitrokeys, also supports NFC)
- FIDO2 and WebAuthn compatibility, allowing use of hardware tokens, Windows Hello, FaceID and other FIDO2 compatible technologies to authenticate users or function as second factor.
- Passwordless login with WebAuthn is supported.
- Gateways: SMS, secure messaging apps Telegram, Signal and more
- Notification (just click to approve login on an existing device like phone)
- Code in an email
- User backup code (User has to generate these in advance and store them in a safe location)
- Administrator backup code (creating those can be delegated to group admins)
- Any number of these can be enabled by the admin.
Active user sessions can be invalidated through a list, by removing the user in the admin settings or by changing passwords. Users can manage their own sessions and devices.
OTP and FIDO2 Nitrokey hardware has been certified with Nextcloud. HSM functionality is being developed.
2FA documentationSingle-sign-on
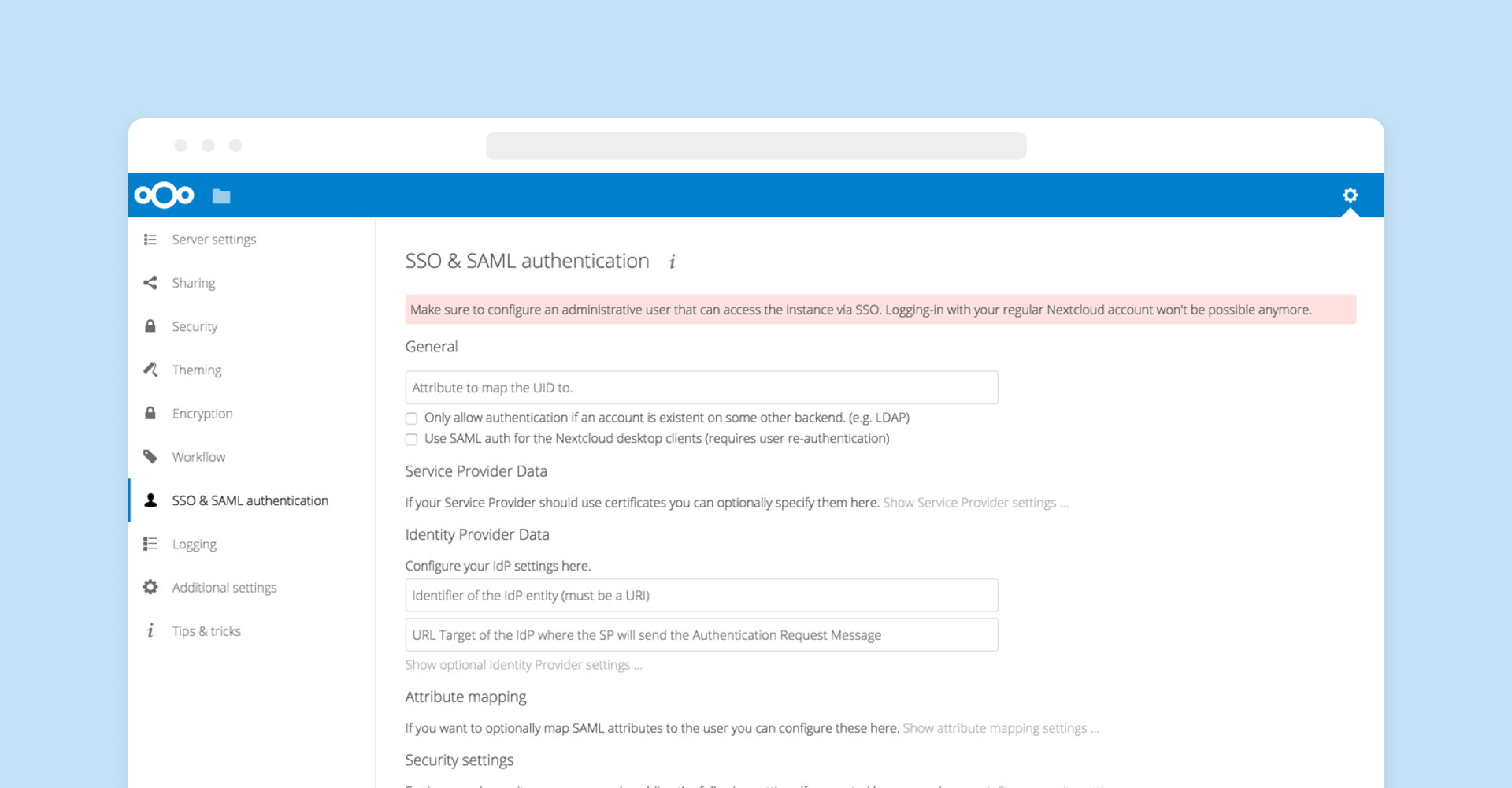
Nextcloud features an SSO & SAML app for easy Single-sign-on integration. SAML 2.0 is supported against OneLogin, Shibboleth, and ADFS. The app also features authentication via environment variables, including support for Kerberos, OAuth2, OpenID and many other mechanisms provided by Apache modules.
The native SAML integration negates the need for external software like Apache modules. Native SAML is compatible with all webservers and supports group memberships, flexible session management and app specific passwords. It can handle multiple Identity Providers and can authenticate to Samba servers with Kerberos.
SSO documentationOther user backends
Nextcloud can work with a number of other backends for authentication and user handling: IMAP, SMB and FTP. These can be used to integrate Nextcloud more easily in company infrastructure. On the app store, more authentication and user backends can be found, like integration with Gluu.
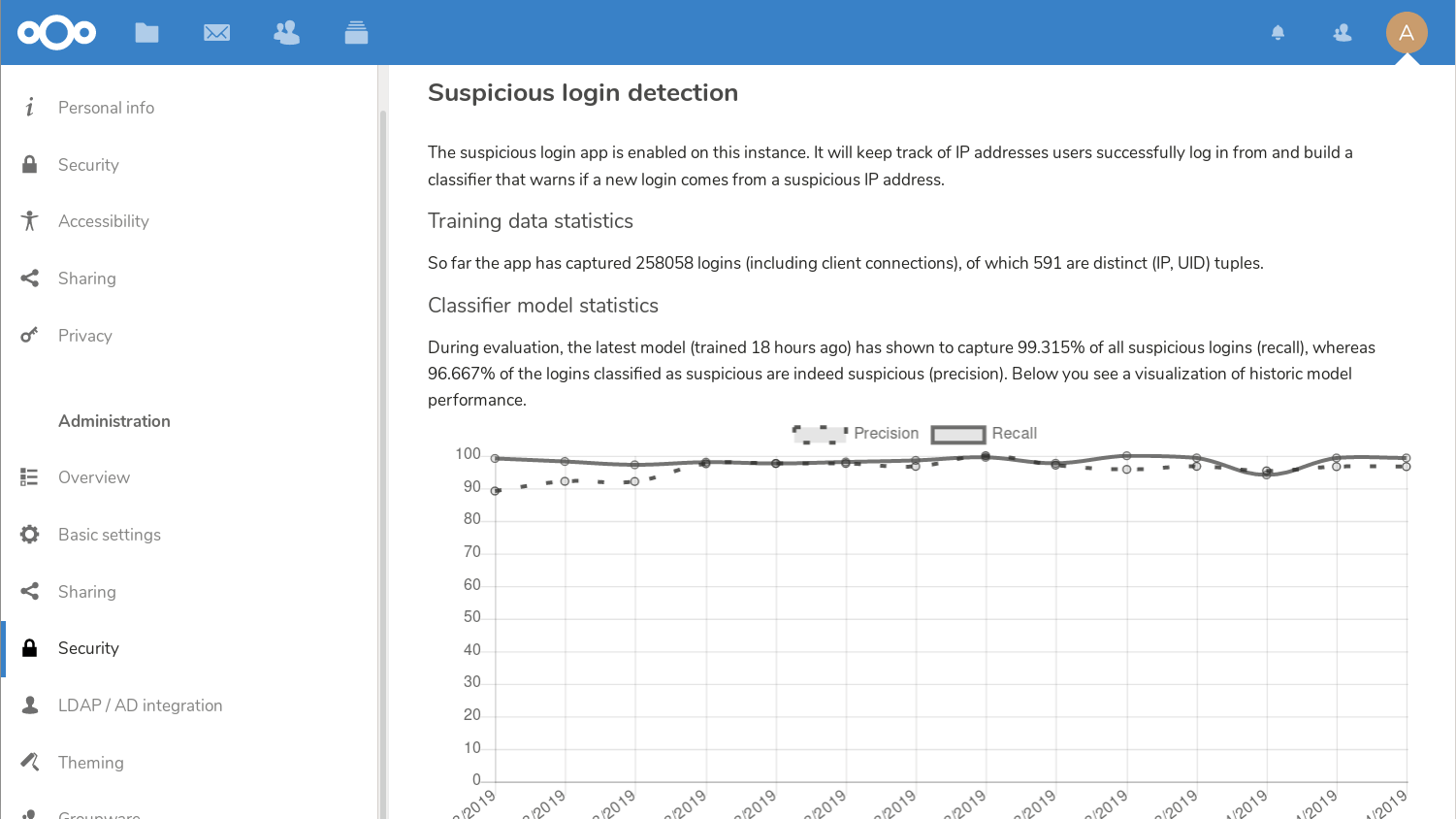
App storeMachine learning based suspicious login detection
Nextcloud includes a machine learning technology which trains a neural network on successful logins on the instance and uses it to classify login attempts. Should it detect a login classified as suspicious by the trained model, it will notify the user and store an entry in the log for the system administrator.
When the user is notified, they can terminate the suspicious session, and proceed to set a new password. The administrator can also take action, like disabling user accounts or forcing users to pick a new password.
Of course, the solution is designed to protect privacy and all data remains on your server!
Learn more