In response to internal demand for collaboration and sharing, companies are moving to cloud-based enterprise file synchronization and storage (EFSS) services that enable users to freely create, manage, organize, and share data within and across organizational boundaries.
Some of the biggest EFSS suppliers include Google Drive, Microsoft OneDrive, and Dropbox. But using EFSS as a service has some serious issues. Privacy and security of sensitive data is a particular challenge with the upcoming General Data Protection Regulation (GDPR) in Europe which will go in effect in May 2018. Growing ransomware attacks and directed criminal and state-sponsored cyber attacks are also on the rise. Events like Brexit or uncertainty around the Privacy Shield data exchange deal with the USA pose a legal risk for the IT admins who have to avoid storing sensitive data in certain countries.
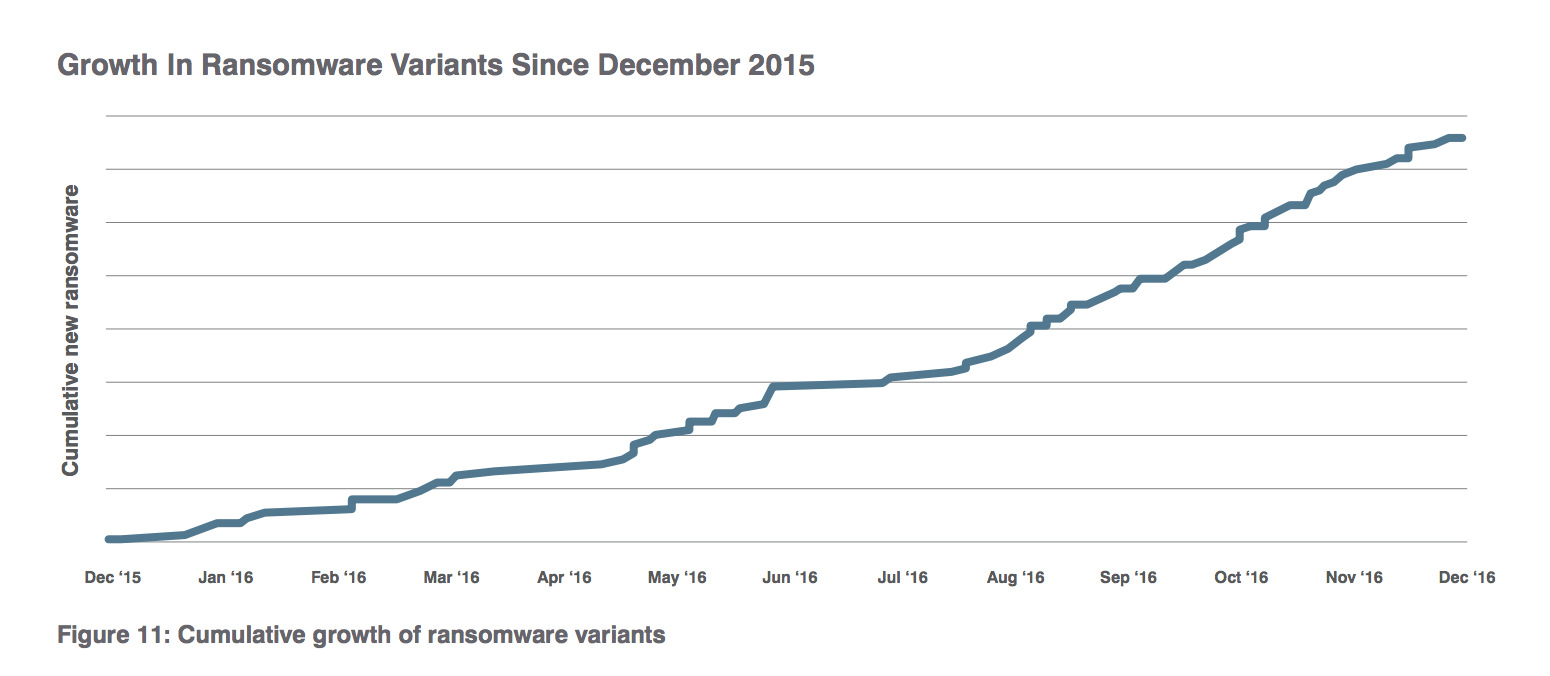
graph from a Proofpoint threat analysis
We provide you three main points to consider when picking an EFSS solution.
Legal issues
Once you sign up for a service, who owns your data? If you pick a hosted solution, you have to accept their terms of services. The vendor has access to your data and can even block you from accessing your own data. They can be compelled to share your data with governments, gag orders forbidding them from telling you about it. And your partners or business customers‘ data are at risk too! You have to ensure you are compliant for current and future regulation, as having to migrate to another solution is rarely easy or affordable. The best way to avoid these murky waters of legal mumbo jumbo is by keeping data either in your own datacenter or at a trusted server provider based in your own country. But how do you pick a good provider that keeps you safe on the legal side?
Make sure you check:
- What sensitive data might be processed and where is it currently stored
- That the solution you pick enables you and your employees to act in compliance with local regulations
- That you have processes in place to protect privacy and deal with problems
Security
When was the last time your file sync and storage provider informed you of a data breach? Never. There was a massive breach of Dropbox in 2012, but we didn’t know about it until 2016 and this turns out to be rather typical in the industry. Reality check: no software is immune to bugs and security breaches. When you use EFSS as a service, you can’t count on getting informed about a breach, nor might you get timely fixes or access to mitigation.
Even self-hosted solutions are at a risk there: vendors are often hostile to security researchers reporting vulnerabilities. And many invest little in security features beyond what gets them marketing attention.
A few factors to consider:
- Does the vendor develop its software in a secure way? A transparent process with security reviews of new designs, code reviews and use of pen-testing tools all help avoid bugs in the process of writing code.
- Have these processes been verified by an independent third party? It is worth downloading a report and flipping through it and checking what the conclusions were.
- Is there a public Security Bug Bounty program with relevant payouts? On security platforms like HackerOne, you can easily check statistics of responsivity and payments, giving you an idea of how serious a vendor takes security.
- How is their security track record? Security mistakes are rarely heavily advertised but you can often find reports by independent researchers complaining their findings were not taken seriously. Or you find issues mentioned and discussed on prominent security lists like the famous Full Disclosure list. A search in the archives can be enlightening!
And a final point: encryption is great. Modern encryption ciphers are rarely broken. Instead, crypto is bypassed! Amazon’s Kindle and Samsung Galaxy protections were bypassed by replacing the key or remove the signature checking code. Bad development practices and a lack of security reviews isn’t fixed with encryption!
I love crypto, it tells me what part of the system not to bother attacking
— Drew Gross, forensic scientist
Future
The market changes quickly and you will need a solution that changes with it. Today you need to share and collaborate. Next year you need to give presentations or have video calls. And you need all this integrated into your infrastructure, in a way you can control.
A simple checklist:
- How well can this solution be integrated into our current infrastructure? Does it support our user directory & authentication, existing storage solutions, monitoring and security processes, auditing and compliance checks?
- Can this solution grow with us? Will it allow us to open an office in another country or even continent and will we be able to keep our processes and sharing working within the legal boundaries, like keeping data localized?
- Can I easily move from one vendor to another? This is relevant not just for your files but also the associated metadata: comments, older versions, sharing information and so on.
- Does the vendor have a healthy development process and are new capabilities that we might need in the future being developed? The world changes and while vendors sometimes excuse little investment in development with “focus on stability”, being a customer of a company that is merely ‘milking’ its customer base is no fun. You’ll end up with a solution that won’t meet your needs, forcing you into a costly migration.
Conclusion
All three focus issues have something in common: transparency of the vendor helps you as a customer. Having access to the code you run on your own or rented servers; being able to see security processes take place in real life; being able to see and perhaps even participate in development. These three factors are how Open Source solutions uniquely help you with legal and security issues and prepare you for the future.
And while there are many prominent Open Source Enterprise File Sync and Share solutions, one stands out. Started by the visionary founder of ownCloud, together with a large team of experienced engineers, Nextcloud is taking the EFSS market by storm.
In the year since its founding, it has established itself as the leading solution for companies looking for a first class security and scalability in a self-hosted technology that facilitates sharing and collaboration. And the large ecosystem of partners and contributors around Nextcloud has developed over 80 applications adding features and capabilities, from authentication and external storage mechanisms to online collaboration and infrastructure integrations.
Picking the right EFSS vendor is not an easy feat. Focus on your legal needs and pick a vendor with a healthy development and strong security expertise to ensure you won’t end up on the list of companies hit by data leaks. Pick a winner that keeps your data safe!


