End-to-end encryption
Protecting data from source to destination
Nextcloud features an enterprise-grade, seamlessly integrated solution for end-to-end encryption. It enables users to pick one or more folders on their desktop or mobile client for end-to-end encryption. Folders can be shared with other users and synced between devices but are not readable by the server.
Note: our end-to-end encryption solution is under constant development. Some features part of the design have not yet been implemented in the client or server code. In particular, as of May 2022, offline recovery, sharing and HSM features are on the roadmap with no fixed date.
Ultimate protection
Nextcloud end-to-end encryption offers the ultimate protection for your data, making it suitable for your most private information. Use it to protect a copy of your passport, passwords, driver’s license or bank account information.
Enterprises could require employees to keep a subset of the most confidential information client-side encrypted. Research, customer information or strategic documents can be guaranteed to be kept confidential.
Seamless integration and ease of use with key features like offline recovery keys, auditing and HSM support make Nextcloud End-to-end Encryption the perfect complement to other Nextcloud security features including Server-side Encryption and File Access Control.
Unique capabilities


- Any number of folders can be end to end encrypted.
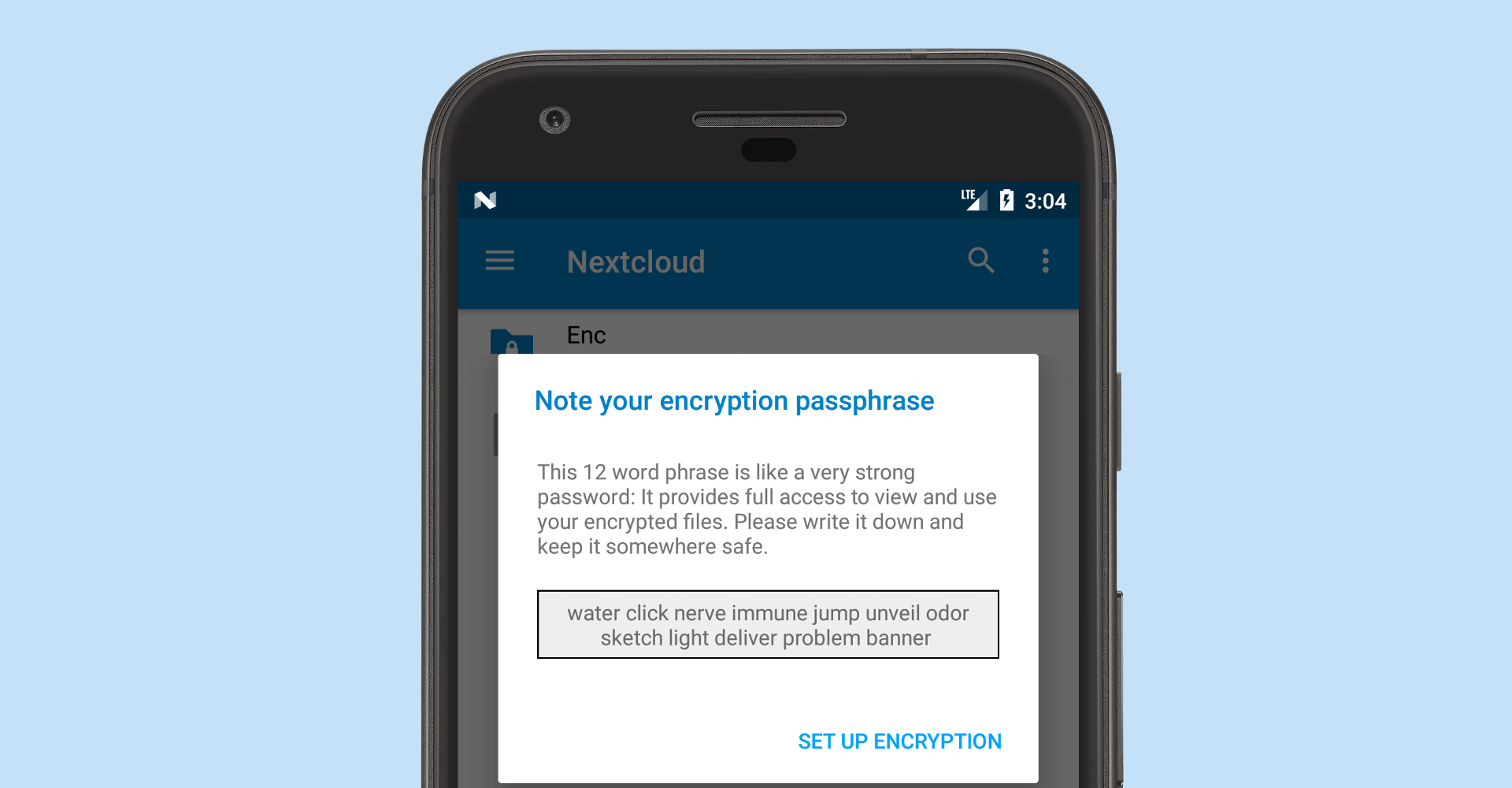
- Easily add a new device with a strong passcode consisting of 12 dictionary words.
- Secure sharing with other users without the need to enter passwords. (not yet implemented)
- Efficient sharing and revoking shares without the need to re-encrypt large files. (not yet implemented)
- Supports a Hardware Security Module for enterprise environments which enables securely issuing new keys to users. (not yet implemented)
- Supports an offline administrator recovery key to be kept in a physically separated location. Users get warned when this key is enabled. (not yet implemented)
- Supports a complete audit log without compromising end to end security.
- Can be combined with our File Access Control to block specific file types or files by specific user groups from uploading unless they are end-to-end encrypted.
Cryptographic Identity Protection
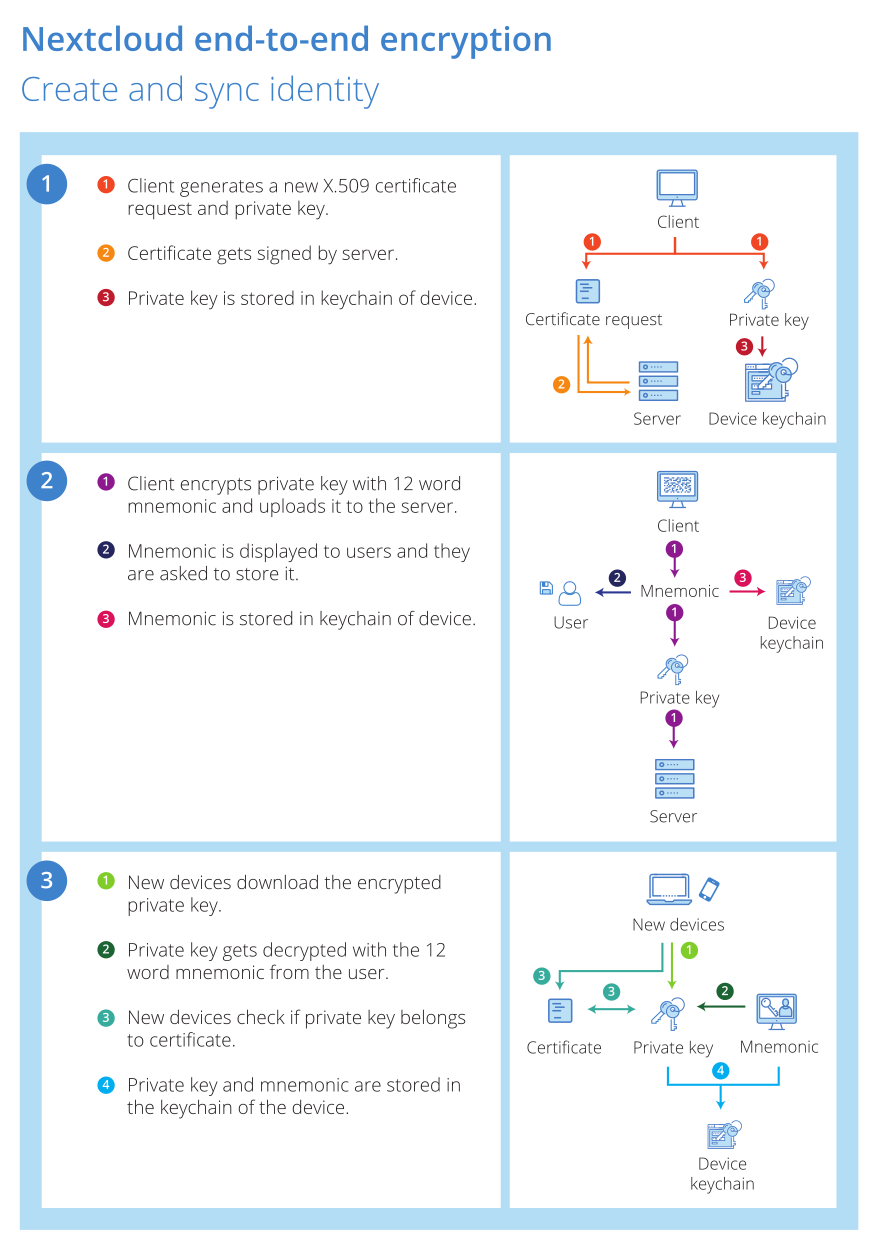
Every user gets a unique public/private key combination when they first enable end-to-end encryption. The public key is sent to the server and signed into a certificate. The certificate is checked by the users’ other clients and used by other users to share encrypted files with the first user, based on Trust On First Use.
- Each device of the user can aid in recovering their private key. Only if a key is lost on all devices AND the 12 secure key words are lost, the user loses access to his/her data. The optional offline administrator recovery key can still be used to re-gain access.
- By default, keys can’t change so as to protect the identity of users from hacking if the server is compromised. If the key could change, a hacker could issue a ‘new’ certificate for the user and have clients respond by re-encrypting data with the new, compromised key.
- The process enables a complete audit log, crucial for enterprise use.
- The certificate can optionally be issued by a Hardware Security Module so it is possible to issue new certificates for existing users in a secure way.
Enterprise-grade encryption solution
Nextcloud offers a supremely easy to use, well integrated file sync and share solution with an uniquely layered approach to security. Our solution delivers deep infrastructure integration with support for nearly any storage technology and combines it with powerful server-side encryption and end-to-end encryption in the clients, both of which can be applied in a granular way.
Rather than making it an either-or choice, businesses can rely on utmost security where it is needed but keep collaborative online document editing and full-text search on the server over the rest of the stored data.
Use cases
Users can access data on a FTP drive shared with another company; while data stored on an external S3 compatible object storage could be encrypted using server-side encryption so the storage provider has no way to compromise their security.
And with the Nextcloud File Access Control feature, files from the HR department can always be enforced to be end-to-end encrypted on their clients, protecting their data from even the worst case of a full server breach. Similarly, sensitive research, customer information or strategic documents can be guaranteed to be kept even from server administrators.
Technical background
Below we cover some of the basics of our design. Download our whitepaper for more details.
Enabling encryption
The encryption is based upon an asymmetric cryptographic system. Every user has exactly one private and public key pair.
The key generation process is designed to keep the contents of the private key from the server while storing it security so it can be synced to other devices the user owns. Some other properties of the process:
The user creates an identity which is signed by the server (using a certificate) and associated with their public key. Users can only have one identity, other clients will refuse to accept a new certificate following the Trust on First Use (TOFU) model. This protects data from a malicious server which tries to generate a new identity for a target user and get clients to re-encrypt the data against it.
In case a user loses their device they can easily recover by using the mnemonic passphrase. The mnemonic passphrase can also be shown in the client settings in case the user forgets their mnemonic. Displaying the mnemonic requires the user to enter their PIN/fingerprint again on mobile devices.
Sharing on folder-level granularity must be possible to individual users. No passwords should need to be exchanged for sharing. Key exchange should be auditable. Adding devices should be easy and new devices should have access to all previously encrypted data.
The protocol needs to support versioning in case of future changes to metadata or crypto handling. Design should support a hardware security module, giving strong authentication, tamper-resistance and a complete audit trail.
Encrypting files
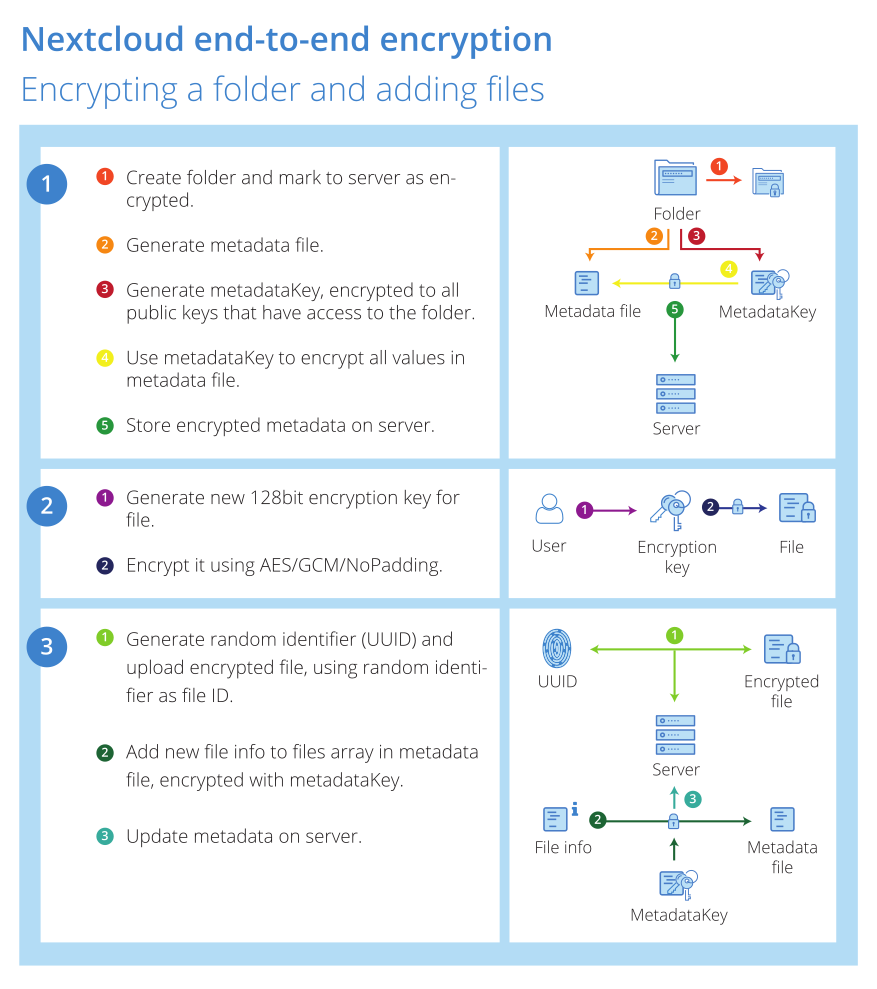
Creating an end-to-end encrypted folder is done by flagging an empty folder as end-to-end encrypted, creating metadata, encrypting and uploading it. The process is protected by locking, with the client requesting a lock from the server and releasing it again after all changes are finished and uploaded.
Files are each encrypted with their own, unique key, which is stored in the metadata file. All data in the metadata file is, in turn, securely encrypted and files names and directory structures are also hidden from the server using a unique UUID as name for each file.